With this guide to thwarting thieves, whether online or on the street, you can protect your privacy, data, and peace of mind.
1. Keep Apps up to date

Update your phone
When it comes to protecting yourself against hackers, step one is always to install software updates as soon as they become available: that’s as true on smartphones as it is on computers. Yes, updating can be a tiresome and intrusive process, and it sometimes brings annoying changes to the interface that you’re used to. All the same, a huge proportion of successful hacks exploit vulnerabilities that have already been patched; exposing yourself unnecessarily is just daft.
When it comes to protecting yourself from hackers, the first step is always to install software updates as soon as they become available: this is true for both smartphones and computers. Yes, updating can be a time-consuming and inconvenient process that results in annoying changes to the interface you’re used to. Nonetheless, a large proportion of successful hacks exploit previously patched vulnerabilities; exposing yourself unnecessarily is foolish.
I would also strongly advise against using unofficial tools to “root” your phone (also known as “jailbreaking” on iOS) unless you are certain of what you are doing. Technical safeguards on a rooted phone can be bypassed, allowing apps to perform normally prohibited actions – including spying or snooping on your personal data.
2. Be careful of what you install

Carefull what you install
When you install a smartphone app, you may be asked to grant it permissions such as reading your files, accessing your camera, or listening in on your microphone. These capabilities have legitimate uses, but they are potentially vulnerable to abuse: think before you approve the request. This is especially true for Android users, as Google’s app-vetting process is less stringent than Apple’s, and there have been reports of malicious apps remaining on the Play Store for months before being discovered and removed.
Android also allows you to install apps from third-party sources, which allows services like Amazon’s competing Appstore to function, but it also allows rogue apps to get onto your phone. I strongly advise you not to install anything from an unknown website.
3. Review what’s already on your phone
Even if the apps on your phone appeared to be simple and safe when you first installed them, subsequent updates may have transformed them into something more sinister. Take two minutes to go through all of the apps on your phone and see what permissions they’re using: on iOS, you’ll find a wealth of information under Settings > Privacy.
It’s more difficult to see which apps have which permissions on Android, but there are plenty of security apps that can help, including free packages from Avast and McAfee. These tools can also intervene and warn you if you attempt to install a malicious app or if a “phishing” attack attempts to trick you into entering a password into an untrusted app or webpage.
4. Make it hard for intruders

Android-security-apps
If a thief gains physical access to your phone, they can cause havoc. For starters, your email app most likely contains a wealth of personal information. When not in use, make sure your phone is locked: both Android and iOS can be configured to require a six-digit passcode. Other options, such as fingerprint or facial recognition, may be available on your device. Such methods aren’t perfect – a determined hacker could copy your fingerprints from a drinking glass or fool a camera with a photograph of you – but they’re far superior to nothing.
Also, be wary of “smart unlock” features that unlock your phone when you’re at home or when your smartwatch is nearby; these could allow a thief to bypass your unlock code entirely.
5. Get prepared to track and lock your phone
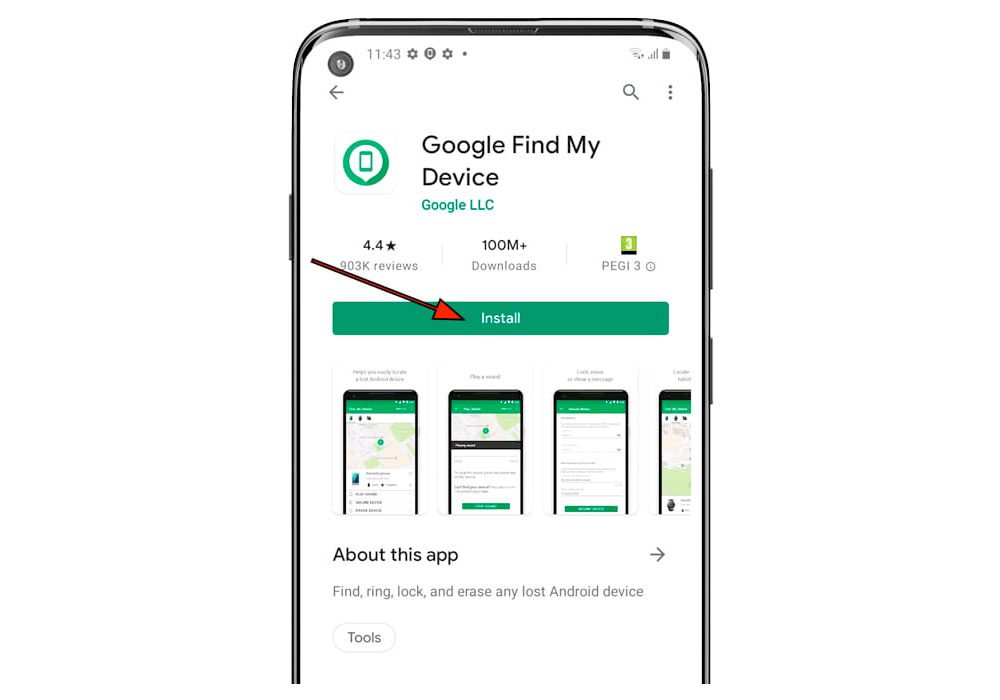
Track-my-phone
Plan ahead of time so that even if your phone is stolen, your data is secure. One option is to program your phone to erase itself after a certain number of incorrect passcode attempts.
If that seems a little extreme, keep in mind that both Apple and Google have “find my device” services that can locate your phone on a map and remotely lock or erase it. This is accessed by Apple users via the iCloud website; you can check if it is enabled on the phone in Settings > iCloud > Find My iPhone. Google’s service is available to Android users at google.co.uk/android/devicemanager. You can also make a missing phone ring, which is useful for drawing attention to the thief or locating a handset that has simply been misplaced.
6. Never leave online services unlocked

online-services-unlocked
Auto-login is a very useful feature, especially since using a virtual keyboard can make typing passwords difficult. It also poses a significant risk: an intruder only needs to open your browser to gain access to all of your online accounts.
Ideally, you should avoid using auto-login features entirely. If you must, use a password manager app that requires you to re-enter a master password on a regular basis. Also, don’t use the same password for more than one app or service: if that one password is discovered, it can be used to gain access to a wide range of private information. Even if you take great care to keep your smartphone secure, hackers regularly break into online services to steal user credentials, which they then use on other sites.
7. Adopt an alter ego
If you’ve followed all of this advice, it should be extremely difficult for anyone to gain access to your phone. However, some major hacks have been carried out with no access to the victim. If someone knows (for example) your date of birth, hometown, and mother’s maiden name – all of which can be easily obtained from a site like Facebook – that’s often all they need to reset your password and begin breaking into your accounts. Such attacks can be avoided by fictionalizing your past with details that are unlikely to be guessed; Perhaps you were born in 1999 to Mrs Victoria Beckham, née Adams, for security reasons. Just keep in mind what you said, or you might end up locking yourself out.
8. Beware open wifi

Beware open wifi
We’re all aware that using an open wireless network carries some risk. However, you may be unaware of how serious the situation is: anyone in the vicinity can eavesdrop on what you’re doing online. This type of attack requires specialized software and skills, so it’s unlikely to be a hazard in your neighborhood cafe, but it’s not something to dismiss.
If you’re unsure about a wireless network, don’t connect; instead, use your phone’s mobile internet connection. Alternatively, use a VPN service such as CyberGhost or TunnelBear (both available free for Android and iOS). These tools route your traffic through a private encrypted channel, so anyone watching your traffic won’t be able to see what you’re up to.
9. Don’t let lockscreen notifications give the game away
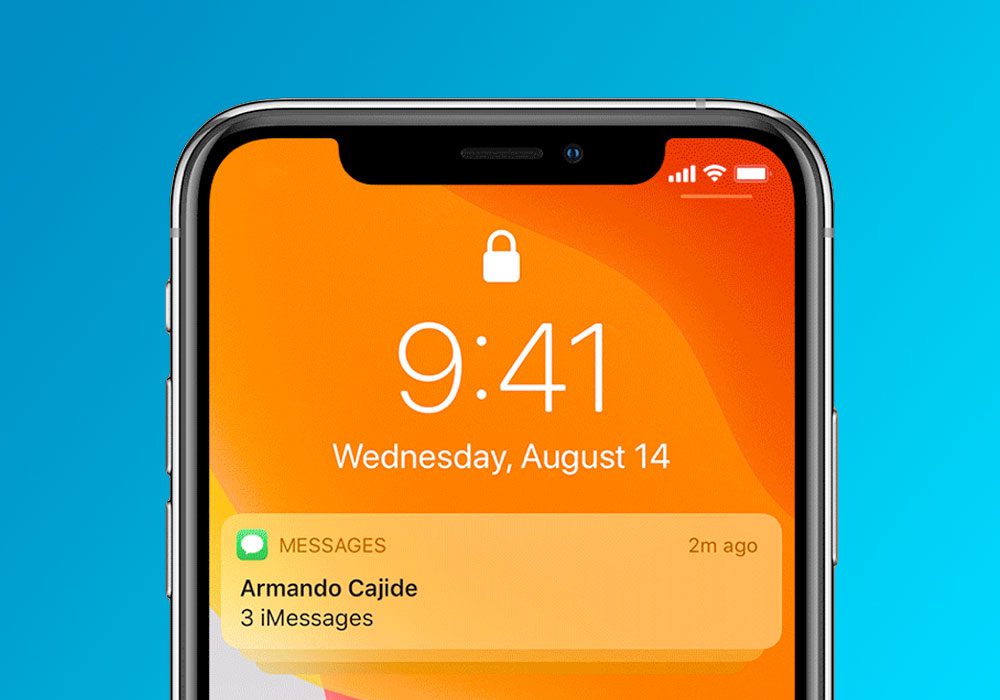
lockscreen notifications
Messages and notifications from various apps appear on your phone’s lockscreen. It’s worth considering what these notifications might reveal. If you work for a large bank, for example, a visible email from a coworker or a meeting reminder alerts a thief that this could be a particularly appealing phone to steal.
Consider disabling Siri access from the lockscreen on iOS. Siri isn’t supposed to reveal personal information before you enter your passcode to unlock your iPhone, but previous hacks have allowed intruders to use Siri to unlock the device, view contact details, and view photos. It’s best to disable the feature entirely: go to Settings > Touch ID & Passcode > Disable Siri on the Lockscreen.
10. Lock individual apps

Lock apps
A strong passcode keeps thieves out of your phone, but what if someone steals it while you’re using it? Or asks to borrow it to check a website before fleeing down the street?
On Android, you can lock individual apps as a second line of defense, so that even if someone gets past your lockscreen, they can’t open your email or banking app without a second password. This feature isn’t built into the operating system, but there are plenty of free apps that do, such as AVG AntiVirus Free. iOS users cannot directly lock individual apps, but Folder Lock, which is available for free on the App Store, can password-protect your documents and folders, limiting the amount of information a thief can access.
11. Get a warning when your phone goes walkies (Missing)
If you’re on the fence about purchasing a smartwatch, consider this little-known feature: If your Apple Watch or Android Wear device loses Bluetooth contact with your phone, it will notify you immediately. If you receive this notification while in a public place, it’s likely that someone has just picked your pocket and is currently stealing your phone.
When the connection drops, the device is usually less than 50 meters away, so the warning allows you to immediately ring the phone, hopefully drawing attention to the thief and prompting them to abandon it. If that fails, you can lock it before the intruder has a chance to break in and steal your data.
12. Keep an eye on things behind the scenes
You can’t completely eliminate the risk of your phone being hacked, no matter how cautious you are, unless you refuse to install any apps or visit any websites. What you can do is use an online service to supplement your on-device security measures. LogDog is an app for both Android and iOS that monitors your identity on sites like Gmail, Dropbox, and Facebook. It notifies you of suspicious activity, such as logins from unfamiliar locations, giving you the opportunity to intervene and change your credentials before serious harm is done. As an added bonus, LogDog will scan your email and highlight messages containing sensitive data such as credit card numbers and passwords, which you can then purge to prevent them from falling into the wrong hands.
Views: 77